IT Security Office
Scam Alerts
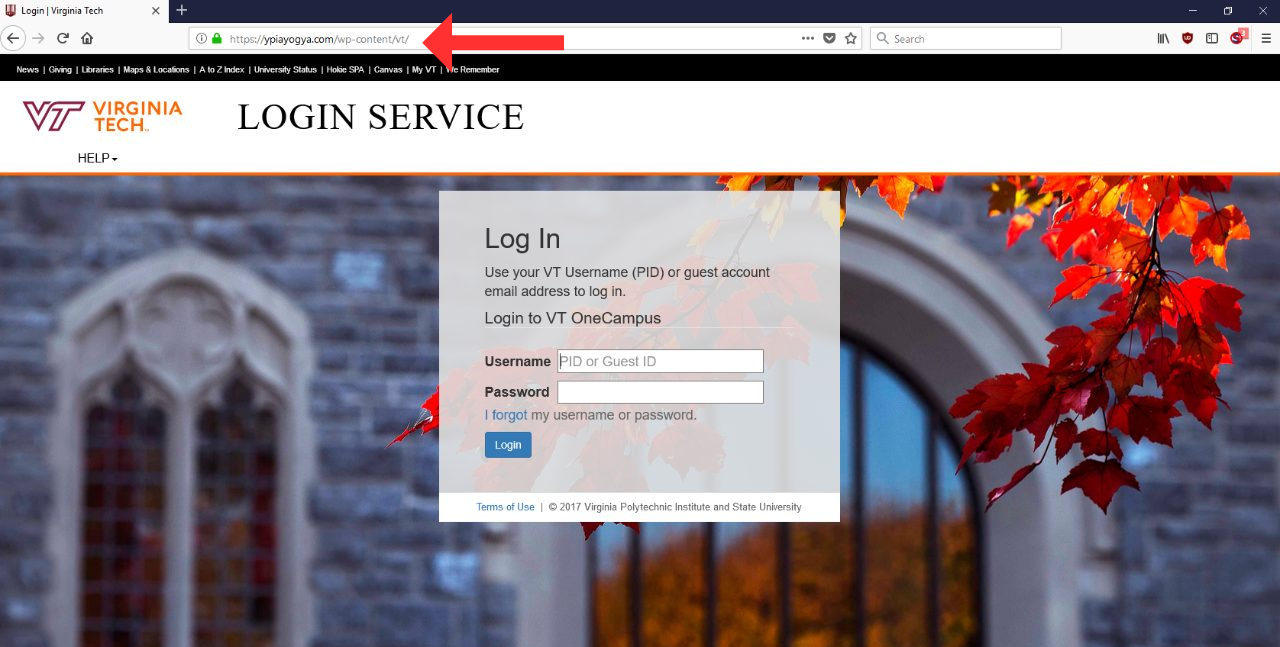
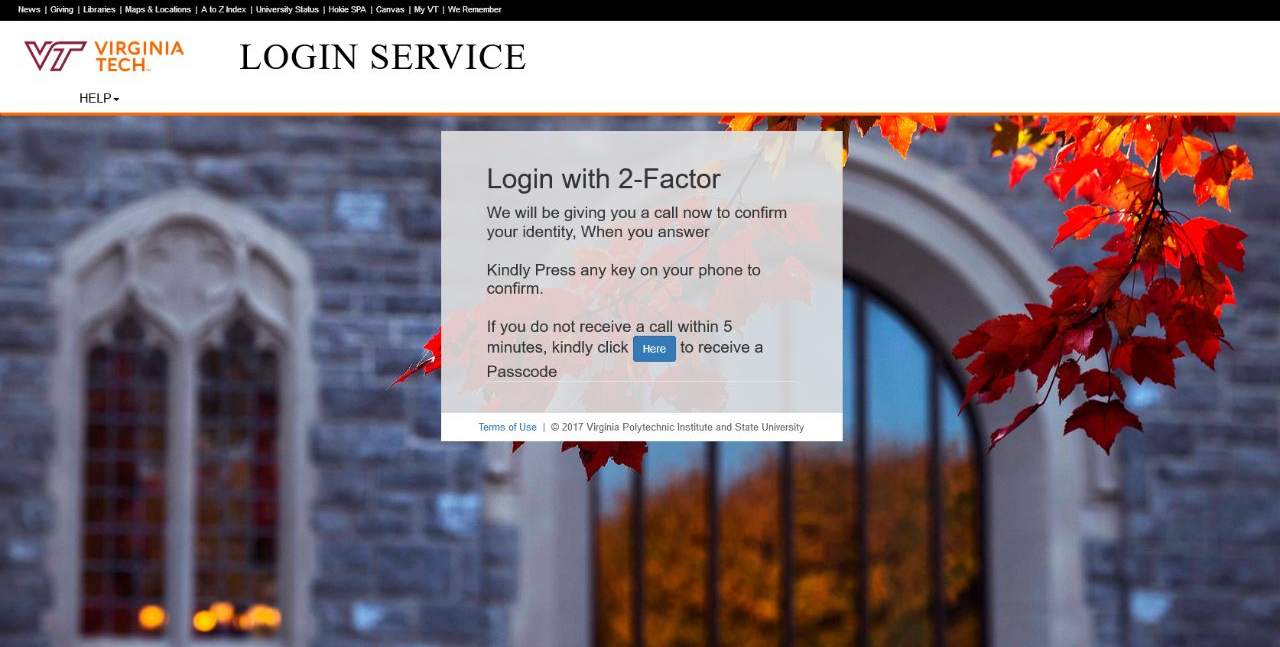
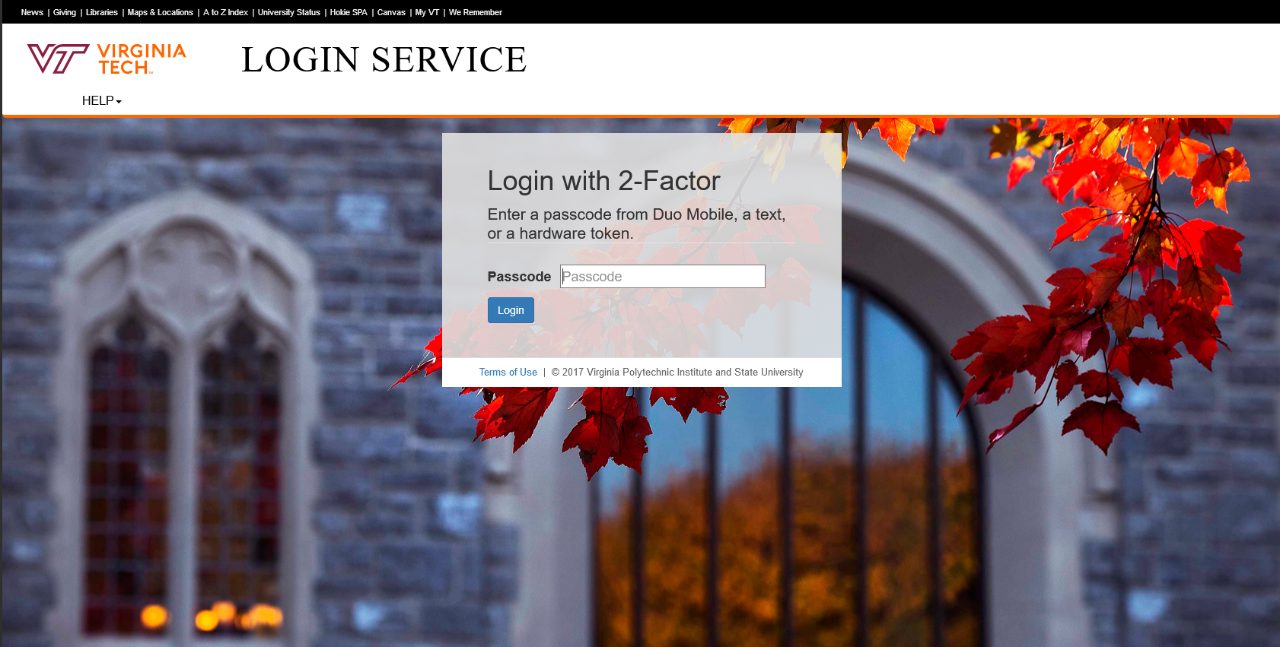
Beware of Fake Websites!
Always check the URL of the pages you visit, especially links found in emails. Attackers can easily replicate websites, like the Virginia Tech Login page within seconds, and try to send you to a fake version of it in order to steal your credentials.
SANS Internet Storm Center, InfoCON: green
The ISC relies on an all-volunteer effort to detect problems, analyze the threat, and disseminate both technical as well as procedural information to the general public. Thousands of sensors that work with most firewalls, intrusion detection systems, home broadband devices, and nearly all operating systems are constantly collecting information about unwanted traffic arriving from the Internet. These devices feed the DShield database where human volunteers as well as machines pour through the data looking for abnormal trends and behavior. The resulting analysis is posted to the ISC’s main web page where it can be automatically retrieved by simple scripts or can be viewed in near real time by any Internet user.
In many ways, the ISC parallels the data collection, analysis, and warning system used by weather forecasters. For example, the National Weather Service uses small sensors in as many places as possible to report pressure, wind speed, precipitation and other data electronically to regional weather stations."